Purpose
Learn about Tulip's general security policies.
Security is core to Tulip's software, operations, infrastructure, and processes. We use industrial standard best practices for security, encryption, and threat management.
Infrastructure
Tulip's cloud runs on Amazon Web Services, or Microsoft Azure, depending on region availability and choice during deployment. Both provide the best-in-class data center and infrastructure security. For AWS, Tulip servers are in an AWS Virtual Private Cloud, protected by Security Group firewalls. Administrative access is protected by both short lived access keys and IP whitelisting. All Tulip AWS and other cloud accounts are protected by strong password and multi-factor authentication. Amazon's data centers meet numerous compliance requirements, including ISO 27001, SOC, PCI, and FedRAMP.
Encryption
All data sent to and from Tulip over the public internet is encrypted in transit via TLS using the strongest recommended cipher suites. Tulip's TLS configuration received an A+ grade from Qualsys's SSLLabs. All data stored by Tulip, including apps, analytics data, and uploaded assets, is encrypted at rest using 256-bit AES.
Data Storage
Data is stored by Tulip in AWS's S3 and RDS services, as well as MongoDB Inc.'s MongoDB Atlas service. Tulip employs a formal process for reviewing third-party vendors that handle customer data, to ensure they they meet or exceed Tulip's data security standards.
Application
Tulip follows web application best-practices, including those recommended by OWASP. Tulip uses HSTS to ensure encryption-in-transit, DOM templating and CSP to avoid XSS, X-Frame-Options to prevent clickjacking, and localStorage instead of cookies to avoid CSRF attacks. Server-side ACL enforcement is enforced via code review, as well as off-the-shelf and custom-built static analysis tools. Passwords are hashed using SHA-256 client-side and then re-hashed using bcrypt server-side.
Process
All production code is reviewed by multiple engineers. Tulip undergoes regular penetration tests by third-party security firms. Tulip performs regular internal security reviews and employs a documented software development process.
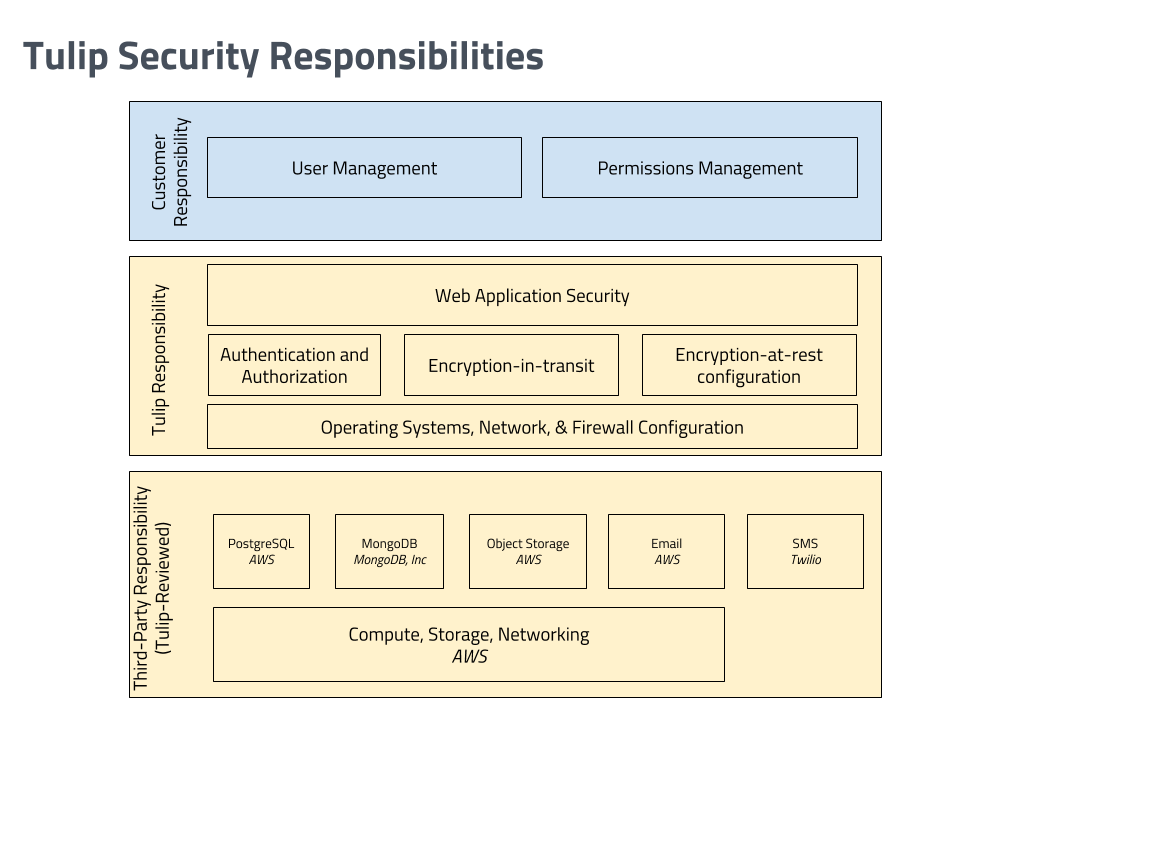
Shared Security Model
Tulip employs a shared security model to establish responsibility across Tulip, our customers, and our third-party vendors.
Further Reading
See our IT Security Policy

