This article covers the more technical aspects of Tulip Connector Hosts. It is intended for individuals with a background in Information Technology (IT).
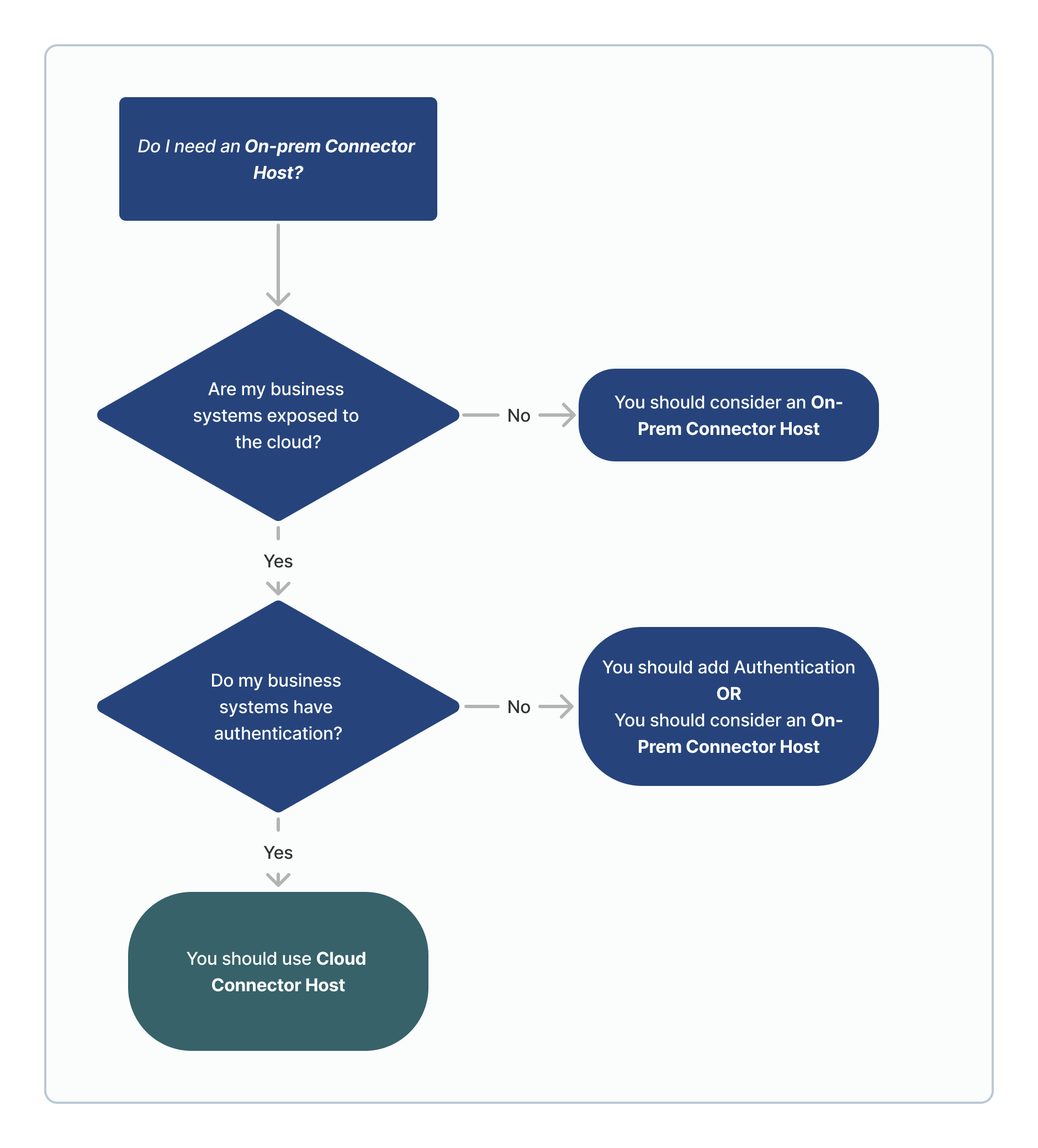
What is the Tulip Connector Host?
Tulip Connectors enable your Tulip Apps to interface with external systems such as databases, APIs, and machines. For more information on our Connectors module, refer to this article: Introduction to Connectors.
The Tulip Connector Host is the component of the Tulip platform that facilitates connections to these external services.
To use the Connectors module, a Connector Host must establish an outbound connection from the Connector Host and an inbound connection to the external system.
Where does the Tulip Connector Host Software Run?
Cloud Connector Host
The most common deployment option is a Cloud Connector Host, which is included in your Tulip subscription and deployed alongside the Tulip Platform. It is available for use on the Connectors Page as “Cloud Connector Host”.
Connection requests from the Cloud Connector Host come from an IP address within Tulip’s Classless Inter-Domain Routing (CIDR) block, allowing customers to allowlist access from the Tulip Connector Host to their service. For customers running the entire Tulip Platform on-premise, the Connector Host will make requests from the same IP address as the Tulip Platform, depending on your deployment configuration.
For more information on Networking Requirements, check out this article.
On-Premise Connector Host
The second, less common, deployment option is an On-Premise Connector Host. In this scenario, a customer hosts the Connector Host within their own network infrastructure, eliminating the need to allow incoming connections from Tulip’s CIDR block. Instead, the Connector Host creates an outgoing connection from your network that is inbound to Tulip.
Key considerations for an On-Premise Connector Host (OPCH) can be found in this article. The diagram below provides guidance on when an OPCH is generally recommended:
What Ports Do I Need to Open to Allow the Cloud Connector Host to Access My System?
The network connection between the Connector Host and your external system is managed by you as the end customer. For questions, consult your internal teams. Default ports for many common services are listed below for convenience:
Databases:
- PostgreSQL: TCP/5432
- Microsoft SQL Server: TCP/1433
- Oracle: TCP/1521
HTTP:
- HTTP: TCP/80
- HTTPS: TCP/443
Machine Protocols:
- OPC UA: TCP/4840
- Kepware OPC UA: TCP/49320
What Are the Security Issues of Opening Access to My DB, API, or OPC UA Server to the Tulip Cloud Connector Host?
To securely connect a DB, API, or OPC UA server to Tulip, follow these best practices:
- Firewall: Open your firewall to only Tulip IP addresses (listed here).
- Encryption: Use SSL/TLS encryption with trusted certificate authorities to protect against Man-in-the-Middle (MitM) attacks.
- Authentication: Implement strong authentication schemes for your APIs and databases, such as strong passwords.
- Access Control: Limit access for users within your databases, APIs, and OPC UA servers, including read-only users and access to specific schemas, tables, endpoints, tags, etc.
- Monitoring: Host your resources on infrastructure with advanced monitoring to detect, alert, and mitigate malicious requests, addressing DDoS attacks.
These suggestions are a starting point and do not replace personalized security planning.
For further assistance, contact your Account Manager or reach out to our support team through the Support Request or Live Chat option using the Help button in the top right of the screen.
Did you find what you were looking for?
For additional help, visit community.tulip.co to post your question or see if others have faced similar issues.



