This document is highly technical in nature and should be reviewed with your IT department.
Recommendations for Machine Monitoring Architecture with Tulip
Tulip is a Frontline Operations Platform that provides a cloud service to its customers. At Tulip, communication between the Tulip Cloud and machines on the Shop Floor is facilitated through the use of a Tulip Connector Host and an OPC UA Server or MQTT Broker running on a customer's internal network.
The Tulip Connector Host acts as the connection point between the Tulip Platform and any third party service accessible over HTTP, SQL, MQTTT, and OPC UA protocols. You can find more information about the Tulip Connector Host in this document.
OPC UA Servers and MQTT Brokers provide machine aggregation and communication translation services. If you are looking for OPC UA Server software, Tulip has found that PTC KEPServerEX can reliably deliver in this market.
Tulip Cloud Connector Host
Most of Tulip's customers make use of the Tulip Cloud Connector Host to establish a connection to their OPC UA Server.
There are two reasons that most of our customers choose the Tulip Cloud Connector Host:
- Bi-weekly Updates
- Better Support.
To establish communication between the Tulip Cloud Connector Host and an internal OPC UA Server or MQTT Broker, a customer must set up a port forwarding rule on their network. A diagram describing this machine monitoring architecture is provided below.
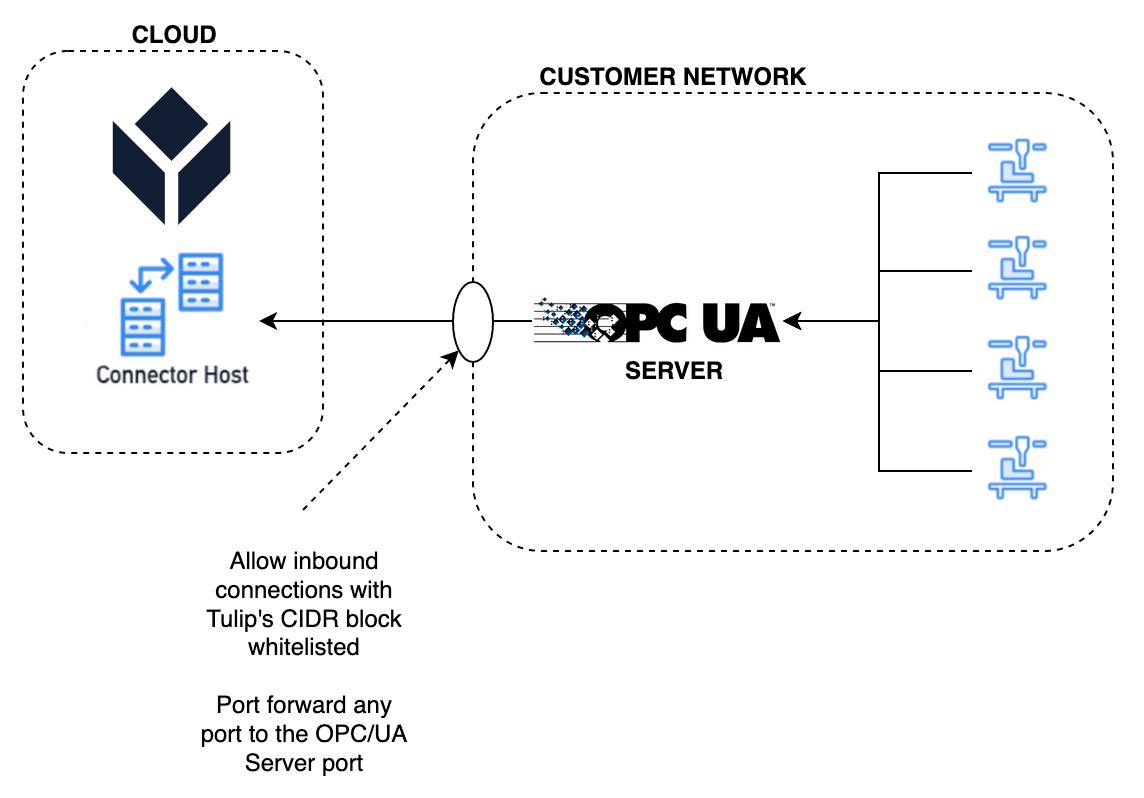
Port forwarding a connection to your OPC UA Server or MQTT Broker
Port forwarding is a networking technique that's used to give external, public devices access to computer services on internal, private networks. We recommend that all of our customers set up port forwarding on their network router to facilitate communication between the Tulip Cloud Connector Host and the respective data source.
A socket, comprised of an IP address and a port, identifies an application or service on a device within a TCP/IP network.
The IP address identifies the device uniquely in the network and the port identifies the application or service running on that device. The combination of the IP address and the port allows multiple applications or services to run on any one device.
The NAT (network address translator) runs on the customer's network router and maps the source (public) IP and port to a destination (private) IP and port.
Once this mapping has been made, external, public devices like the Tulip Cloud Connector Host sends TCP/IP packets to the source (public) IP address and port. The NAT router maps those packets and re-transmits them to the destination (private) IP address and port.
As a security precaution, we ask all of our customers to whitelist Tulip's Cloud IPs and blacklist all other IP addresses for the specified source IP and port. This is to ensure that only the Tulip Connector Host can communicate with the OPC UA server running on the customer's network.
For the NAT mapping to be persistent, the server that is running the OPC UA Server will need to have a static IP assigned to it.
On-Premise Connector Host
Some of Tulip's customers have networking requirements that limit their ability to make use of cloud products.
In this case, Tulip can provide a customer's network with a Tulip Connector Host for executing communication internally on a customer's network. With this option, the inbound network requirement becomes an outbound network requirement as described in the diagram below.
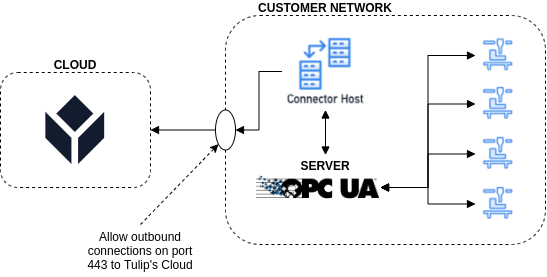
Please additionally review this document for more requirements surrounding the installation and configuration of a Tulip On-Premise Connector Host.

