- Print
Here's how Tulip Account Owners can work with LDAP to manage users in their account.
This feature is only available to existing customers, and is no longer offered to new Tulip customers.
In this article, you will learn:
- How Tulip can connect to your Active Directory instance
- Different ways to configure the Active Directory integration
- Technical requirements for an Active Directory integration
Tulip currently integrates Microsoft’s Active Directory product via the LDAP protocol. If your organization uses Active Directory, then you can manage your Tulip users based on rules from Active Directory.
Tulip User Overview
Tulip has two different user interfaces:
- Tulip, where apps are built and edited, and which can be connected to external databases
- The Tulip Player, where users and operators run the apps that were built in Tulip
A User's permission level is defined by a User Role.
Tulip has multiple levels of user privileges. For information on these roles please see: Managing User Roles in Tulip
- Account Owners & various other listed roles have the ability to edit apps in Tulip
- Operators only have access to run apps via the Tulip Player. They cannot edit apps or access the Tulip interface.
LDAP Integration Options
To integrate LDAP with Tulip, you can either manage your Users roles based on Active Directory groups, or from within Tulip:
- Managing User Roles from Active Directory groups: You'll need to appropriately group your users based on their desired permission level on your Active Directory Server, and provide your Tulip System Administrator with the appropriate mapping (Ex: Group A = Account Owners). This means that both authorization and authentication are determined by your IdP.
- Managing User Roles from within Tulip: You'll need manually add each user from within Tulip, with their specified User Role, and have them create their account with the exact username that's in your Active Directory. This means that only authentication is controlled by your IdP.
There are four separate ways that you can configure your integration:
If Operators are managed in your IdP
- Require all Tulip users to log into Tulip or Tulip Player using their Active Directory username and password. Roles within Tulip are specified based on Active Directory groups. Authorization and authentication via LDAP.
- Require all Tulip users to log into Tulip or Tulip Player using their Active Directory username and password. Roles are maintained within Tulip. Authentication only via LDAP.
If Operators are not managed in your IdP
- Allow Tulip Operators to log into Tulip Player using only their badge ID, but require Tulip Account Owners & other roles to log into Tulip using their Active Directory username and password. Roles within Tulip are specified based on an Active Directory group. Authorization and authentication via LDAP.
- Allow Tulip Operators to log into Tulip Player using only their badge ID, but require Tulip Account Owners & other roles to log into Tulip using their Active Directory username and password. Roles are maintained within Tulip. Authentication only via LDAP.
You can choose the configuration option based on your organization’s security protocols. Please not that enforcing the use of Active Directory username and password for all Tulip users is the most secure option.
Coordinating Tulip Users With LDAP Users
Managing User Roles from within Tulip
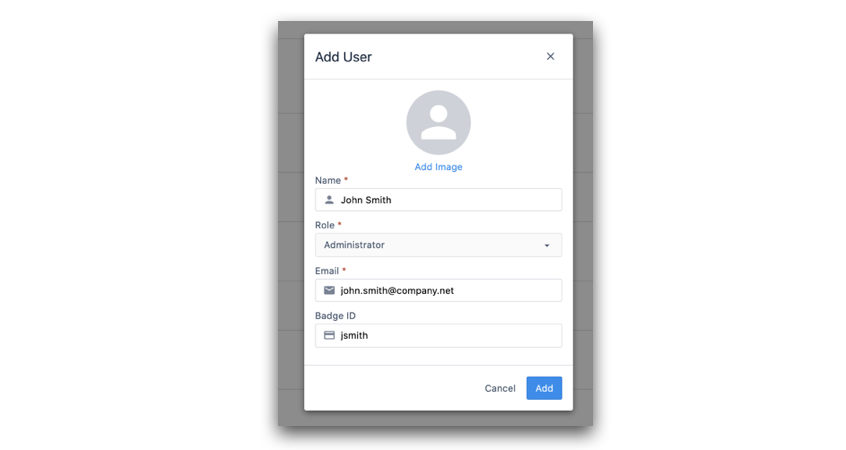
If your organization chooses to manage User Roles from within Tulip, a Tulip Account Owners will first need to create a new user Then, they must add a Tulip username that matches their LDAP username. Any email is acceptable.
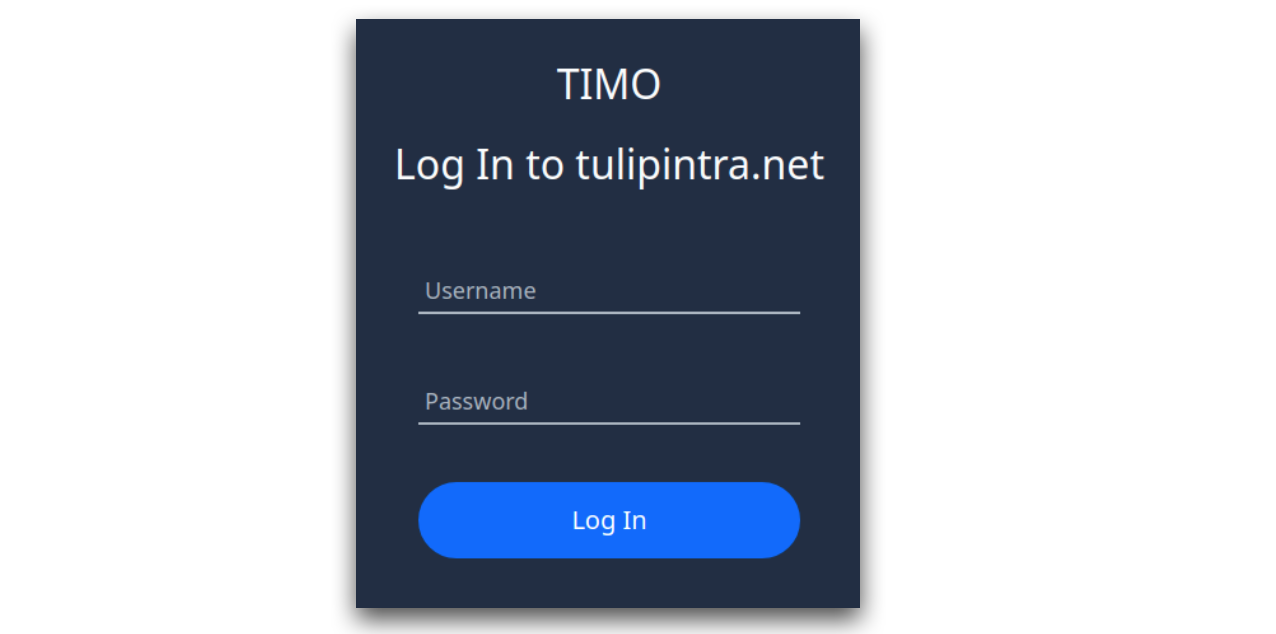
When this Tulip user attempts to log in, they will need to add their LDAP username in the “Username” field, and their password in the “Password” field. Tulip will then authenticate them in your Active Directory instance. The login screen will look like the following:
In this case, a Tulip System Administrator will add your first Tulip user with the information that you provide.
Managing User Roles from Active Directory groups
If your organization chooses to define Tulip roles based on Active Directory groups, then there is no need to create individual users within Tulip. Instead, you can provide the names of your user groups and their mapped Tulip User Roles.
When the user logs into Tulip with their Active Directory credentials for the first time, Tulip will authenticate them with your Active Directory instance and then automatically create an account within Tulip. As mentioned previously, their capabilities will be dependent on their Active Directory group and what you've defined the group's mapped role to be.

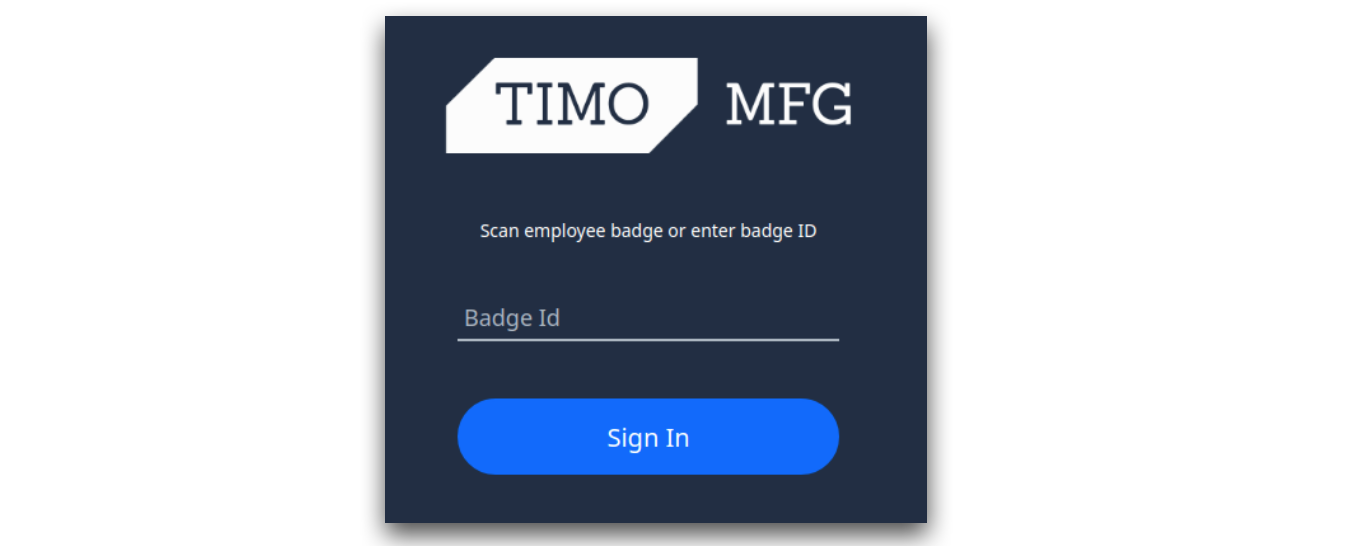
If you choose a configuration option where Tulip Operators are allowed to log in using their badge ID, the Operator login screen in the Tulip Player will look like the following:
Technical Requirements
To configure an LDAP connection, you will need to provide your own LDAP server that is accessible by Tulip's Server and provide the following information:
- The server address (e.g.
ldaps://xxx.xxx.xxx:636) - A "Distinguished Name" to search (e.g.
dc=tulip,dc=co) - The Certificate Authority used to sign the certificates of the LDAP server
Your IT System Administrator should be easily able to provide this information.
Summary
To configure the LDAP integration for your Tulip Account, please start by reaching out to your customer account representative with the following information:
- Which of the 4 previously mentioned authentication methods would you like to use.
- If applicable: A list mapping your Active Directory groups and their desired Tulip User Roles
- The technical requirements in the previous section.
- A window of time in which you'd like to make the change. Note that all clients will be logged out when the change is made and that everyone will need to re-authenticate to your Tulip site.



